Share your quitting journey
- EX Community
- Conversations
- Journals / Blogs
- How to Prevent Phishing - off Topic
How to Prevent Phishing - off Topic
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
A friend sent me the following information and I thought it very important for all of us. I've edited it slilghty to take out certain links. If you want to read the whole thing go to: https://www.wordfence.com/blog/2017/01/gmail-phishing-data-uri/
Wide Impact: Highly Effective Gmail Phishing Technique Being Exploited
A new highly effective phishing technique targeting Gmail and other services has been gaining popularity during the past year among attackers. Over the past few weeks there have been reports of experienced technical users being hit by this.
This attack is currently being used to target Gmail customers and is also targeting other services.
The way the attack works is that an attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.
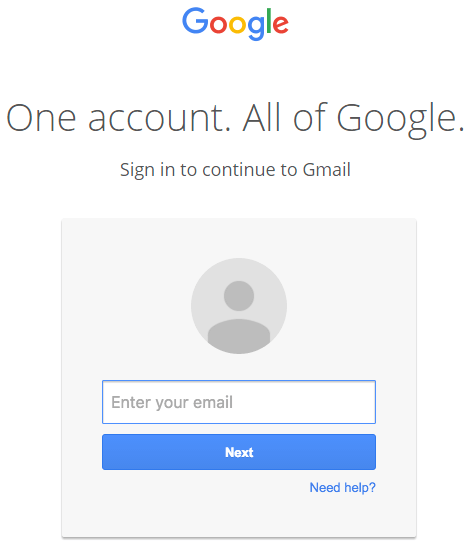
You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….
You go ahead and sign in on a fully functional sign-in page that looks like this:
Once you complete sign-in, your account has been compromised. A commenter on Hacker News describes in clear terms what they experienced over the holiday break once they signed in to the fake page:
“The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
The attackers signing into your account happens very quickly. It may be automated or they may have a team standing by to process accounts as they are compromised.
Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot.
Now that they control your email address, they could also compromise a wide variety of other services that you use by using the password reset mechanism including other email accounts, any SaaS services you use and much more.
What I have described above is a phishing attack that is used to steal usernames and passwords on Gmail. It is being used right now with a high success rate. However, this technique can be used to steal credentials from many other platforms with many variations in the basic technique.
How to protect yourself against this phishing attack
You have always been told: “Check the location bar in your browser to make sure you are on the correct website before signing in. That will avoid phishing attacks that steal your username and password.”
In the attack above, you did exactly that and saw ‘accounts.google.com‘ in the location bar, so you went ahead and signed in.
To protect yourself against this you need to change what you are checking in the location bar.
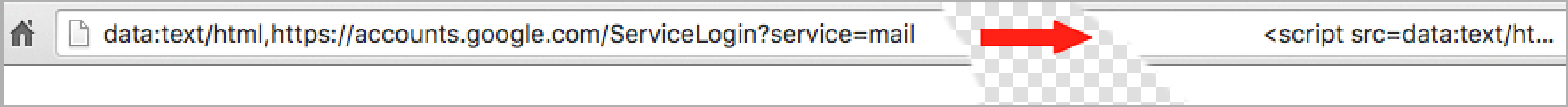
This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. When you glance up at the browser location bar and see ‘data:text/html…..’ that is actually a very long string of text. If you widen out the location bar it looks like this:
There is a lot of whitespace which I have removed. But on the far right you can see the beginning of what is a very large chunk of text. This is actually a file that opens in a new tab and creates a completely functional fake Gmail login page which sends your credentials to the attacker.
As you can see on the far left of the browser location bar, instead of ‘https’ you have ‘data:text/html,’ followed by the usual ‘https://accounts.google.com….’. If you aren’t paying close attention you will ignore the ‘data:text/html’ preamble and assume the URL is safe.
You are probably thinking you’re too smart to fall for this. It turns out that this attack has caught, or almost caught several technical users who have either tweeted, blogged or commented about it. There is a specific reason why this is so effective that has to do with human perception. I describe that in the next section.
How to protect yourself
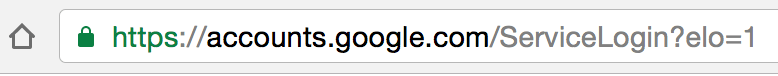
When you sign in to any service, check the browser location bar and verify the protocol, then verify the hostname. It should look like this in Chrome when signing into Gmail or Google:
Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take special note of the green color and lock symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.
Enable two factor authentication if it is available on every service that you use. GMail calls this “2- step verification” and you can find out how to enable it on this page.
Enabling two factor authentication makes it much more difficult for an attacker to sign into a service that you use, even if they manage to steal your password using this technique. I would like to note that there is some discussion that indicates even two factor authentication may not protect against this attack. However I have not seen a proof of concept, so I can not confirm this.
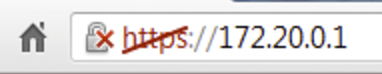
Google have modified the behavior of the address bar in the past to show a green protocol color when a page is using HTTPS and a lock icon to indicate it is secure.
They also use a different way of displaying the protocol when a page is insecure, marking it red with a line through it:
During this attack, a user sees neither green nor red. They see ordinary black text:
That is why this attack is so effective. In user interface design and in human perception, elements that are connected by uniform visual properties are perceived as being more related than elements that are not connected...
In this case the ‘data:text/html’ and the trusted hostname are the same color. That suggests to our perception that they’re related and the ‘data:text/html’ part either doesn’t matter or can be trusted.
Update: How to check if your account is already compromised
I’ve had two requests in the comments about this so I’m adding this section now. (at 9:39am Pacific time, 12:39am EST).
There is no sure way to check if your account has been compromised. If in doubt, change your password immediately. Changing your password every few months is good practice in general.
If you use GMail, you can check your login activity to find out of someone else is signing into your account. Visit https://support.google.com/mail/answer/45938?hl=en for info. To use this feature, scroll to the bottom of your inbox and click “Details” (very small in the far lower right hand corner of the screen). This will show you all currently active sessions as well as your recent login history. If you see active logins from unknown sources, you can force close them. If you see any logins in your history from places you don’t know, you may have been hacked.
Spread the word
By Mark Maunder
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Helping Adult Quit
13 -
Helping Child Quit
11 -
Longtime Quit
880 -
Preparing to Quit
275 -
Quitting Chewing
17 -
Quitting Medicinal Nicotine
15 -
Quitting Smoking
363 -
Quitting Tobaccoless Pouches
10 -
Quitting Vaping
174 -
Recently Quit
431 -
Staying Quit
173 -
Trying Again
172 -
Undecided
19